Page Not Found
Page not found. Your pixels are in another canvas.
A list of all the posts and pages found on the site. For you robots out there is an XML version available for digesting as well.
Page not found. Your pixels are in another canvas.
About me
This is a page not in th emain menu
Published:
This post will show up by default. To disable scheduling of future posts, edit config.yml and set future: false.
Published:
This is a sample blog post. Lorem ipsum I can’t remember the rest of lorem ipsum and don’t have an internet connection right now. Testing testing testing this blog post. Blog posts are cool.
Published:
This is a sample blog post. Lorem ipsum I can’t remember the rest of lorem ipsum and don’t have an internet connection right now. Testing testing testing this blog post. Blog posts are cool.
Published:
This is a sample blog post. Lorem ipsum I can’t remember the rest of lorem ipsum and don’t have an internet connection right now. Testing testing testing this blog post. Blog posts are cool.
Published:
This is a sample blog post. Lorem ipsum I can’t remember the rest of lorem ipsum and don’t have an internet connection right now. Testing testing testing this blog post. Blog posts are cool.
A Z-machine emulator for TI graphing calculators, written in eZ80 assembly.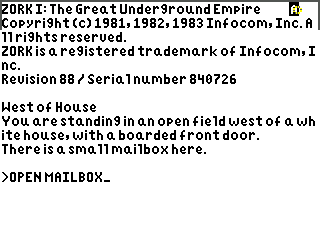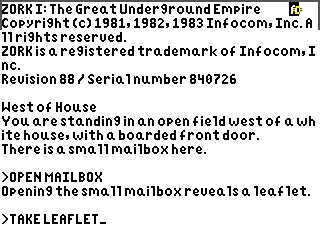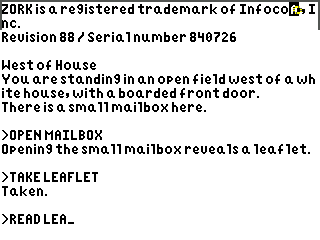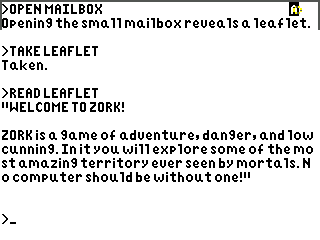
A Turing-complete ROP compiler with a shellcode stack, presented at BSidesLV 2019.
Published in Middlebury College, Department of Mathematics, 2019
Integer factorization is an inherently difficult problem for which there is no known algorithm that produces an answer in polynomial time. Until recently, it was unknown whether the very similar but weaker problem of primality testing is equally difficult. Primality testing is the problem of determining whether an arbitrary positive integer n ∈N is prime or composite. In 2002, Agrawal, Kayal, and Saxena presented a provably correct deterministic primality test that terminates in polynomial time over all N. Although previous polynomial-time algorithms had been presented, they rely upon unproven claims such as the Riemann Hypothesis. We restrict our focus to algorithms that are unconditionally correct. In this paper, we review principles common to existing deterministic, polynomial-time primality tests, specifically Fermat’s Little Theorem (FlT) and the related topic of cyclotomic fields. We introduce a simple primality test based on FlT, and then discuss increasingly advanced algorithms (Pocklington primality test, APR primality test). In the second part of the paper, we prove the correctness of the AKS Primality Test, concluding that primality testing is a problem solvable in polynomial time.
Published in Middlebury College, Department of Computer Science, 2020
Spectre, a class of speculative execution vulnerabilities disclosed in 2018, has demonstrated weaknesses in existing security protections. Attackers can exploit speculative buffer overflows, a Spectre variant, to achieve arbitrary speculative code execution in victims. The security community has not thoroughly explored which security protections speculative buffer overflows can bypass. Previous literature assesses that address space layout randomization (ASLR), a security protection in modern operating systems, effectively mitigates speculative buffer overflow attacks. I present SpectreR2P, a host-based attack that discloses a victim’s ASLR-randomized code address via speculative buffer overflow, thereby demonstrating the ineffectiveness of ASLR against speculative buffer overflows.
Published in ISCA'22, 2022
We propose leakage containment models (LCMs)—novel axiomatic security contracts which support formally reasoning about the security guarantees of programs when they run on particular microarchitectures. Our core contribution is an axiomatic vocabulary for formalizing LCMs, derived from the established axiomatic vocabulary for formalizing processor memory consistency models. Using this vocabulary, we formalize microarchitectural leakage—focusing on leakage through hardware memory systems—so that it can be automatically detected in programs and provide a taxonomy for classifying said leakage by severity. To illustrate the efficacy of LCMs, we first demonstrate that our leakage definition faithfully captures a sampling of (transient and non-transient) microarchitectural attacks from the literature. Second, we develop a static analysis tool based on LCMs which automatically identifies Spectre vulnerabilities in programs and scales to analyze real-world crypto-libraries.
Recommended citation: Nicholas Mosier, Hanna Lachnitt, Hamed Nemati, and Caroline Trippel. Axiomatic hardware-software contracts for security. In Proceedings of the 49th Annual International Symposium on Computer Architecture, ISCA ’22, page 72–86, New York, NY, USA, 2022. Association for Computing Machinery. https://doi.org/10.1145/3470496.3527412
Published in BuildSys'22, 2022
We describe a software system that provides software control of multiple, networked battery energy storage systems in the electric grid. The system introduces two new ideas that enable flexible and dependable management of energy storage. The first is a virtual battery, which can either partition a battery or aggregate multiple batteries. The second is a reservation-based API which allows asynchronous control of batteries to meet contractual guarantees in a safe and dependable manner.
Recommended citation: Sonia Martin, Nicholas Mosier, Obi Nnorom Jr., Yancheng Ou, Liana Patel, Oskar Triebe, Gustavo Cezar, Philip Levis, and Ram Rajagopal. Software defined grid energy storage. In The 9th ACM International Conference on Systems for Energy-Efficient Buildings, Cities, and Transportation (BuildSys ’22), November 9–10, 2022, Boston, MA, USA. ACM, New York, NY, USA, page 218-227. https://doi.org/10.1145/3563357.3564082
Published in PLARCH'23 Workshop at ISCA'23, 2023
Spectre attacks exploit control- and data-flow (mis)prediction on modern processors to transiently leak program secrets. Comprehensively mitigating Spectre leakage is hard, and doing so while preserving the program’s performance is even harder: no existing Spectre mitigations are widely deployed due to their high overhead or high complexity. We claim that a comprehensive, efficient, and low-complexity mitigation for Spectre attacks requires engaging in software-compiler-hardware co-design. In our talk, we will pitch such a co-designed Spectre mitigation that will be widely deployable at a low cost in security-critical applications. As a first step towards this goal, we have developed Serberus, a comprehensive and proven-correct Spectre mitigation for constant-time code that targets existing hardware. We are currently exploring lightweight hardware support to improve Serberus’ performance in other application domains.
Published in S&P'24, 2024
We present Serberus, the first comprehensive mitigation for hardening constant-time (CT) code against Spectre attacks (involving the PHT, BTB, RSB, STL, and/or PSF speculation primitives) on existing hardware. Serberus is based on three insights. First, some hardware control-flow integrity (CFI) protections restrict transient control-flow to the extent that it may be comprehensively considered by software analyses. Second, conformance to the accepted CT code discipline permits two code patterns that are unsafe in the post-Spectre era. Third, once these code patterns are addressed, all Spectre leakage of secrets in CT programs can be attributed to one of four classes of taint primitives—instructions that can transiently assign a secret value to a publicly-typed register. We evaluate Serberus on cryptographic primitives in the OpenSSL, Libsodium, and HACL* libraries. Serberus introduces 21.3% runtime overhead on average, compared to 24.9% for the next closest state-of-the-art software mitigation, which is less secure.
Recommended citation: N. Mosier, H. Nemati, J. Mitchell and C. Trippel, Serberus: Protecting Cryptographic Code from Spectres at Compile-Time, in 2024 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 2024 pp. 48-48. doi: 10.1109/SP54263.2024.00048
Published in arXiv preprint, 2025
We present µSpectre, a new class of transient execution attacks that exploit microcode branch mispredictions to transiently leak sensitive data. We find that many long-known and recently-discovered transient execution attacks, which were previously categorized as Spectre or Meltdown variants, are actually instances of µSpectre on some Intel microarchitectures. Based on our observations, we discover multiple new µSpectre attacks and present a defense against µSpectre vulnerabilities, called µSLH.
Recommended citation: Nicholas Mosier, Hamed Nemati, John C. Mitchell, Caroline Trippel. Analyzing and exploiting branch mispredictions in microcode, arXiv preprint. https://doi.org/10.48550/arXiv.2501.12890
Published in HPCA'26, 2026
We present the Protean Spectre defense—the first to be altogether comprehensive, covering all side channels and speculation; programmer-transparent, requiring no source modifications; and programmable, tailoring its hardware protections to software’s security needs. Several Spectre defenses offer the first two features, but protect a hardware-defined subset of architectural state from transiently leaking. Meanwhile, many Spectre-vulnerable programs process secrets in many ways such that rigid protections cannot both performantly and fully secure. Protean overcomes this limitation through: (1) ProtISA, an ISA extension that allows software to tell which architectural registers and memory bytes require protection from transiently leaking at each program point; (2) ProtCC, a compiler that automatically infers and programs ProtISA protections for vulnerable code with minimal user input; and (3) ProtDelay and ProtTrack, two alternative hardware mechanisms that performantly enforce software-defined ProtISA protections. By flexibly tailoring a hardware Spectre defense to a program’s data protection needs, Protean significantly reduces the overhead of fully securing vulnerable programs. With ProtDelay/ProtTrack, it averages 0.27x/0.18x and 0.42x/0.34x of the runtime overhead of the best secure baseline for programs with and without mixed security needs, respectively, at lower/comparable hardware complexity.
Recommended citation: Nicholas Mosier, Hamed Nemati, John C. Mitchell, and Caroline Trippel. In Proceedings of the 32nd IEEE International Symposium on High-Performance Computer Architecture (HPCA), January-February 2026. (To appear.)
Published:
ropc is a compiler from Turing-complete ROPC-IR to x86_64 shellcode. ROPC-IR is an assembly-like source language of my own invention. The most distinguishing feature of my compiler is that the shellcode program has access to a 2nd stack, called the shellcode stack. Once you have a shellcode stack, much becomes possible, such as subroutine calls within shellcode as well as library calls that don’t mangle the shellcode on the target stack.
Published:
I presented my Axiomatic Hardware-Software Contracts paper at ISCA’22 in New York. Watch a video of the presentation (youtube) or view the slides (pdf, pptx).
Published:
I presented Serberus, our comprehensive Spectre mitigation for constant-time programs that targets existing Intel hardware.
Published:
I presented our in-progress work on developing an efficient, general Spectre mitigation by engaging in hardware-software co-design. This presentation describes ongoing follow-up work to Serberus, our recently published Spectre mitigation that targets existing Intel hardware.
Grader, Middlebury College, Department of Mathematics, 2019
I graded assignments for the undergraduate course MATH225 Linear Algebra and Differential Equations.
Tutor, Middlebury College, Department of Computer Science, 2021
I tutored undergraduates in Systems Programming, a course about writing robust, systems-level C code for UNIX-based systems.